From the good old days of ‘https://en.wikipedia.org/wiki/Phreaking’. We’ve come a long way into the era of digitalisation where cyber security has become a multi-billion dollar industry.
India vs Pakistan skirmishes
On 26 November 2010, a group calling itself the Indian Cyber Army hacked the websites belonging to the Pakistan Army and the others belong to different ministries, including the Ministry of Foreign Affairs, Ministry of Education, Ministry of Finance, Pakistan Computer Bureau, Council of Islamic Ideology, etc. The attack was done as a revenge for the Mumbai terrorist attacks.
On 4 December 2010, a group calling itself the Pakistan Cyber Army hacked the website of India's top investigating agency, the Central Bureau of Investigation (CBI)
In July 2016, Cymmetria researchers discovered and revealed the cyberattack dubbed 'Patchwork', which compromised an estimated 2500 corporate and government agencies using code stolen from GitHub and the dark web. Examples of weapons used are an exploit for the Sandworm vulnerability (CVE-2014-4114), a compiled AutoIt script, and a UAC bypass code dubbed UACME. Targets are believed to be mainly military and political assignments around Southeast Asia and the South China Sea and the attackers are believed to be of Indian origin and gathering intelligence from influential parties.
The Kerala government website was crashed by Pakistani hackers, who posted an image of a burning Indian flag. The hackers had left messages such as "Pakistan Zindabad", "We are Team Pak Cyber Attacker" and "Security is just an illusion".
However, hours later, the Kerala-based 'Mallu Cyber Soldiers' hacked into Pak government websites, warning the pro-Pakistan hackers to "stay away from Indian cyberspace".
The sites crashed by Indian hackers include pakistan.gov.pk, president.gov.pk, and cabinet.gov.pk.
Mallu Cyber Soldiers hacks ISIS
Mallu Cyber Soldiers, the first group of ethical hackers from Kerala, claims to have leaked the cyber details of ISIS terrorists, operating from India. As a test dose, on Thursday, they released the information on a Kashmir-based man, and vowed to publish the entire list on Republic Day.
Sources close to Mallu Cyber Soldiers claimed that they honey-trapped the ISIS sympathizers who are motivating the youth for war. Over 50 Indian hackers were involved in the extensive operation to get access to their encrypted chat via social engineering.
“Despite having concrete information about the ISIS sympathizers or other terror supporters, the government or the intelligence agencies do not pay a heed to it. Instead of conducting a primary investigation, the motive and patriotism of the hackers are questioned,” said Kislay Chaudhary, chairman of NGO Indian Cyber Army.
India vs China skirmishes
UIDAI Data Breach
The Insikt Group said it detected four IP addresses assigned to the Bennett Coleman And Co. Ltd. media company in “sustained and substantial network communications” with two Winnti servers between February and August.
As the group was investigating the Bennett Coleman hack, it said it also identified a compromise in June and July of the Unique Identification Authority of India, or UIDAI, the government agency that oversees the national identification database.
In that case, it detected some 10 megabytes of data downloaded from the network and almost 30 megabytes uploaded, possibly indicating the deployment of additional malicious tooling from the attacker infrastructure.” It suggested such a database could be used by hackers to identify “high-value targets, such as government officials, enabling social engineering attacks or enriching other data sources.”
Chinese also targeted Mumbai based media firms (ToI) and the Madhya Pradesh Police department after the MP CM talked about ‘banning Chinese products’
Power grid hacks
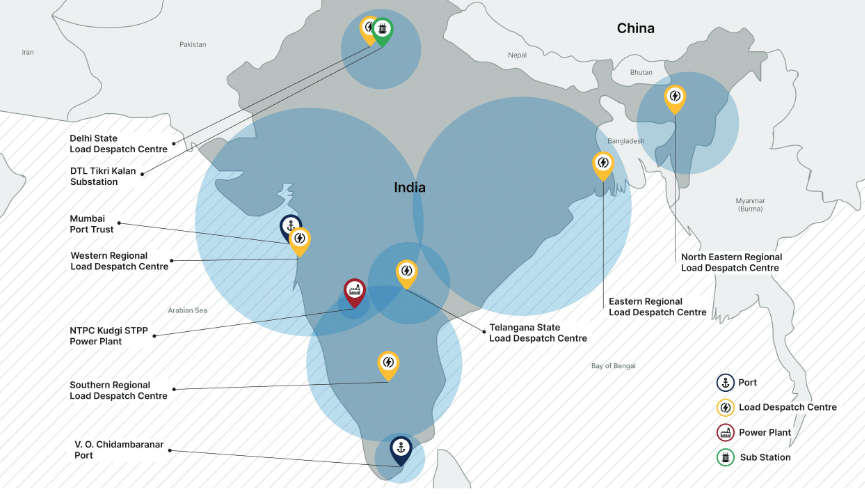
“10 distinct Indian power sector organizations, including 4 of the 5 Regional Load Despatch Centres (RLDC)... have been identified as targets in a concerted campaign against India's critical infrastructure,” said the report. Chidambaranar and Mumbai ports/ power grids were also identified as targets.
The first thing to note is that these attacks were using ShadowPad, which is one of the largest known supply-chain attacks, according to cybersecurity firm Kaspersky.
It is a covert background malware, which hides inside legit software. Once activated, it allows hackers to access the system to install more malicious software or steal data.
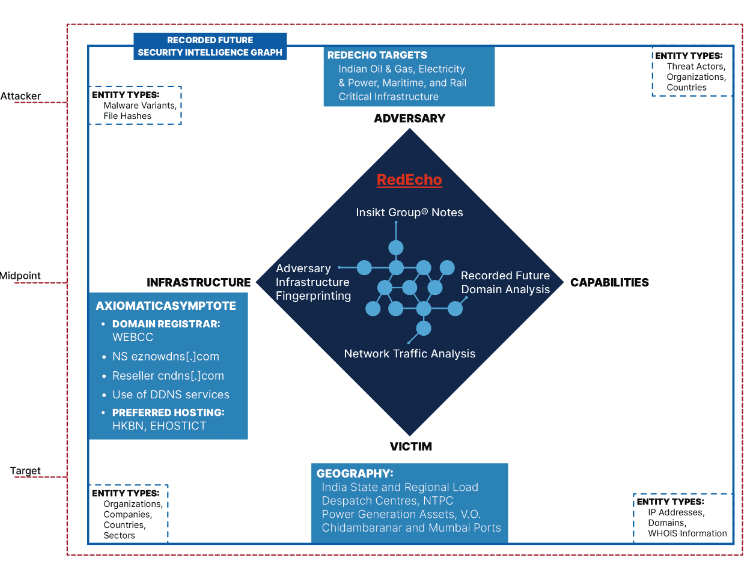
Even though the investigators spotted some overlaps with other cybercriminal groups — like APT41, known for the NetSarang incident using ShadowPad, and Tonto Team — they don’t believe that there is enough evidence to pin the blame on any known perpetrators. In addition to APT41 and Tonto Team, ShadowPad is used by at least three other distinct Chinese groups. So, instead, this closely related but distinct activity group has been dubbed RedEcho.
High profile hacks
A high-profile cyber attack on 12 July 2012 breached the email accounts of about 12,000 people, including those of officials from the Ministry of External Affairs, Ministry of Home Affairs, Defense Research and Development Organizations (DRDO), and the Indo-Tibetan Border Police (ITBP).[117] A government-private sector plan being overseen by National Security Advisor (NSA) Shivshankar Menon began in October 2012, and intends to boost up India's cyber security capabilities in the light of a group of experts findings that India faces a 470,000 shortfall of such experts despite the country's reputation of being an IT and software powerhouse.
Present&Future
Presently, India is building is the necessary cyber security infrastructure required by the various government agencies to target & defend against high-profile cyber attacks.
Great initiatives were taken by the Indian government by setting up DCA (Defence Cyber Agency), C&IS (Cyber and Information Security), NCIIPC (National Critical Information Infrastructure Protection Centre). But it’s too early to comment on their functions as nothing has been released in public.
India vs Pakistan skirmishes
On 26 November 2010, a group calling itself the Indian Cyber Army hacked the websites belonging to the Pakistan Army and the others belong to different ministries, including the Ministry of Foreign Affairs, Ministry of Education, Ministry of Finance, Pakistan Computer Bureau, Council of Islamic Ideology, etc. The attack was done as a revenge for the Mumbai terrorist attacks.
On 4 December 2010, a group calling itself the Pakistan Cyber Army hacked the website of India's top investigating agency, the Central Bureau of Investigation (CBI)
In July 2016, Cymmetria researchers discovered and revealed the cyberattack dubbed 'Patchwork', which compromised an estimated 2500 corporate and government agencies using code stolen from GitHub and the dark web. Examples of weapons used are an exploit for the Sandworm vulnerability (CVE-2014-4114), a compiled AutoIt script, and a UAC bypass code dubbed UACME. Targets are believed to be mainly military and political assignments around Southeast Asia and the South China Sea and the attackers are believed to be of Indian origin and gathering intelligence from influential parties.
The Kerala government website was crashed by Pakistani hackers, who posted an image of a burning Indian flag. The hackers had left messages such as "Pakistan Zindabad", "We are Team Pak Cyber Attacker" and "Security is just an illusion".
However, hours later, the Kerala-based 'Mallu Cyber Soldiers' hacked into Pak government websites, warning the pro-Pakistan hackers to "stay away from Indian cyberspace".
The sites crashed by Indian hackers include pakistan.gov.pk, president.gov.pk, and cabinet.gov.pk.
Mallu Cyber Soldiers hacks ISIS
Mallu Cyber Soldiers, the first group of ethical hackers from Kerala, claims to have leaked the cyber details of ISIS terrorists, operating from India. As a test dose, on Thursday, they released the information on a Kashmir-based man, and vowed to publish the entire list on Republic Day.
Sources close to Mallu Cyber Soldiers claimed that they honey-trapped the ISIS sympathizers who are motivating the youth for war. Over 50 Indian hackers were involved in the extensive operation to get access to their encrypted chat via social engineering.
“Despite having concrete information about the ISIS sympathizers or other terror supporters, the government or the intelligence agencies do not pay a heed to it. Instead of conducting a primary investigation, the motive and patriotism of the hackers are questioned,” said Kislay Chaudhary, chairman of NGO Indian Cyber Army.
India vs China skirmishes
UIDAI Data Breach
The Insikt Group said it detected four IP addresses assigned to the Bennett Coleman And Co. Ltd. media company in “sustained and substantial network communications” with two Winnti servers between February and August.
As the group was investigating the Bennett Coleman hack, it said it also identified a compromise in June and July of the Unique Identification Authority of India, or UIDAI, the government agency that oversees the national identification database.
In that case, it detected some 10 megabytes of data downloaded from the network and almost 30 megabytes uploaded, possibly indicating the deployment of additional malicious tooling from the attacker infrastructure.” It suggested such a database could be used by hackers to identify “high-value targets, such as government officials, enabling social engineering attacks or enriching other data sources.”
Chinese also targeted Mumbai based media firms (ToI) and the Madhya Pradesh Police department after the MP CM talked about ‘banning Chinese products’
Power grid hacks
“10 distinct Indian power sector organizations, including 4 of the 5 Regional Load Despatch Centres (RLDC)... have been identified as targets in a concerted campaign against India's critical infrastructure,” said the report. Chidambaranar and Mumbai ports/ power grids were also identified as targets.
The first thing to note is that these attacks were using ShadowPad, which is one of the largest known supply-chain attacks, according to cybersecurity firm Kaspersky.
It is a covert background malware, which hides inside legit software. Once activated, it allows hackers to access the system to install more malicious software or steal data.
Even though the investigators spotted some overlaps with other cybercriminal groups — like APT41, known for the NetSarang incident using ShadowPad, and Tonto Team — they don’t believe that there is enough evidence to pin the blame on any known perpetrators. In addition to APT41 and Tonto Team, ShadowPad is used by at least three other distinct Chinese groups. So, instead, this closely related but distinct activity group has been dubbed RedEcho.
- An alert by the Computer Emergency Response Team (CERT-in) of India has averted a hacking attempt of the power systems in Telangana’s TS Transco and TS Genco by a China-based group. TS Transco and TS Genco are power utilities of the state
High profile hacks
A high-profile cyber attack on 12 July 2012 breached the email accounts of about 12,000 people, including those of officials from the Ministry of External Affairs, Ministry of Home Affairs, Defense Research and Development Organizations (DRDO), and the Indo-Tibetan Border Police (ITBP).[117] A government-private sector plan being overseen by National Security Advisor (NSA) Shivshankar Menon began in October 2012, and intends to boost up India's cyber security capabilities in the light of a group of experts findings that India faces a 470,000 shortfall of such experts despite the country's reputation of being an IT and software powerhouse.
Present&Future
Presently, India is building is the necessary cyber security infrastructure required by the various government agencies to target & defend against high-profile cyber attacks.
Great initiatives were taken by the Indian government by setting up DCA (Defence Cyber Agency), C&IS (Cyber and Information Security), NCIIPC (National Critical Information Infrastructure Protection Centre). But it’s too early to comment on their functions as nothing has been released in public.
